Sponsored by Proofpoint
Sponsored by NGINX App Security
Prevent Downtime and Breaches by Securing Your Modern Apps and APIs
Sponsored by MetricStream
eBook - IT and Cyber Risk Management : The Accelerated Approach
Sponsored by MetricStream
eBook I 4 Ways to Bolster Cyber Risk Management and Compliance in a Covid-19 World
Sponsored by MetricStream
State of IT and Cyber Risk Management Survey Report 2021
Sponsored by AWS
Creating a Culture of Security
Sponsored by AWS
Achieve Machine Learning Results Faster
Sponsored by AWS
Innovate By Migrating to the Most Secure Cloud
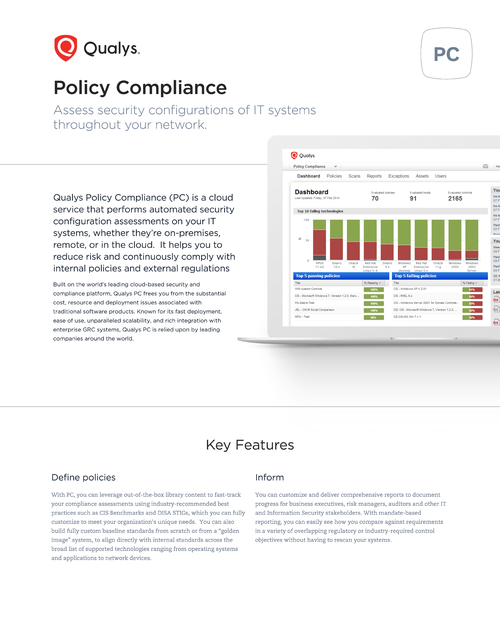
Sponsored by Qualys Inc.
Cloud Based Security & Policy Compliance
Sponsored by Imperva
Cyber Security and Compliance Guide for Financial Services
Sponsored by Dtex Systems
Everyone as a Trusted Insider: An Intelligent Replacement for Employee Monitoring
Sponsored by Dtex Systems
Finding the Disconnect: Perceptions and Behaviors of Today’s Enterprise Employees
Sponsored by LastPass
Identity and Access Management Is Critical to Securing a Remote Workforce
Sponsored by HelpSystems