Cybercrime , Fraud Management & Cybercrime , Security Operations
Twilio and Mailchimp Breaches Tie to Massive Phishing Effort
'Subject X' Suspected in Theft of Nearly 10,000 credentials at 130 Organizations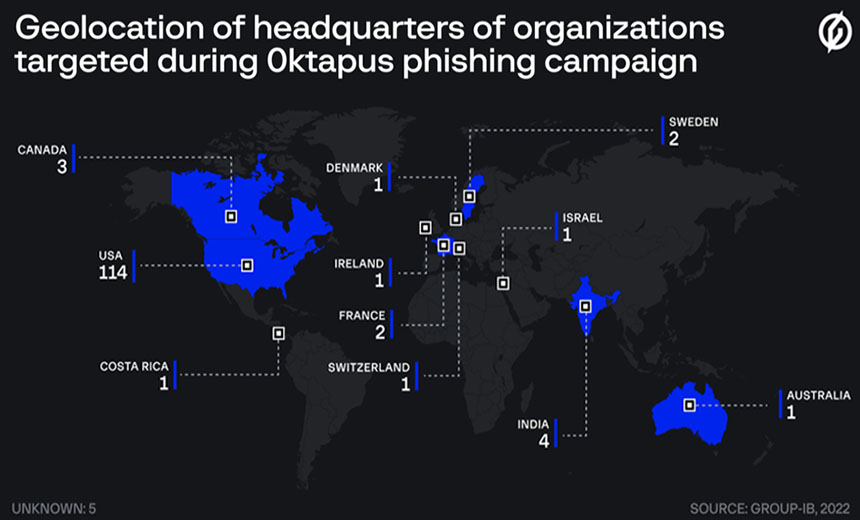
An ongoing phishing campaign that compromised more than 130 organizations is a reminder that even with multi-factor authentication and other defenses in place, attackers will try to trick employees into helping to circumvent them.
The campaign, best known for cracking the security perimeters of customer engagement platform Twilio and email service provider Mailchimp, has been looked for ways to bypass multifactor authentication defenses, oftentimes aiming to steal information tied to cryptocurrency accounts, security researchers say.
Cybersecurity firm Group-IB says it's been tracking the campaign, codenamed 0ktapus and tied it to the recent attacks. Following a trail of Telegram accounts, researchers say they were also able to identify one of its administrators, an "allegedly a 22-year-old software developer" living in North Carolina.
"The initial objective of the attackers was clear: Obtain Okta identity credentials and two-factor authentication - 2FA - codes from users of the targeted organizations," Group-IB, researchers Rustam Mirkasymov and Roberto Martinez say in a new research report. "With this information in hand, the attackers could gain unauthorized access to any enterprise resources the victims have access to."
The phishing campaign involves sending SMS messages to targets to trick them into visiting a fake but real-looking Okta login page that captures their one-time code. Group-IB says it's not clear how attackers got contact details for their initial targets, although they began "targeting mobile operators and telecommunications companies," meaning that "chances are, some phone numbers may have been obtained from those initial attacks."
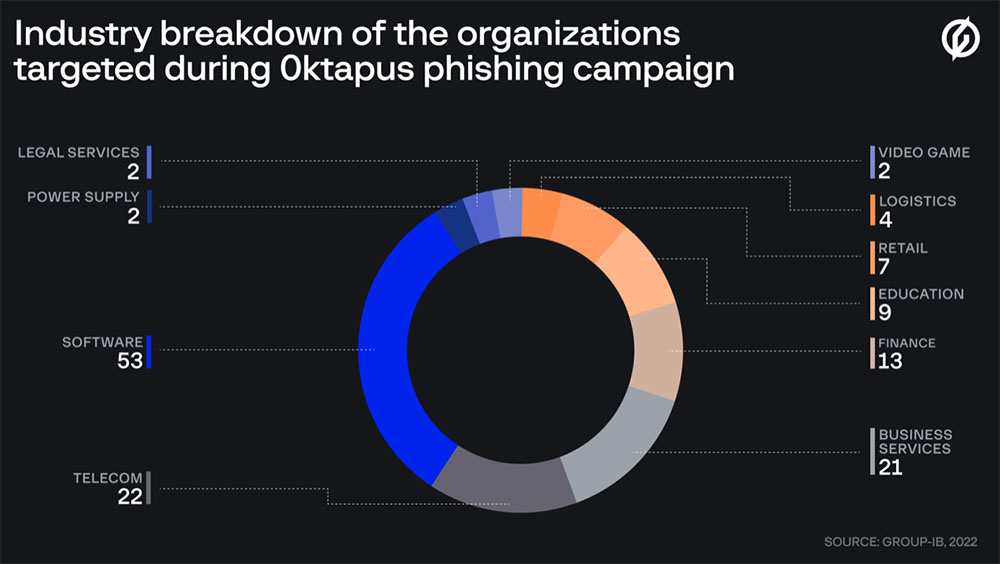
So far 169 different domains have been tied to the phishing campaign, with many of the domain names including words such as "sso, vpn, okta, mfa and help," Group-IB says. "These domains were all used by the attackers to target organizations in multiple industries, located mostly in the United States and Canada."
Some of the domains that appear to have been registered by the same attackers include variations on the names of organizations that include Acronis, Avast, Broadcom, Citrix, Eset, Fortinet, Microsoft, Mozilla and Sophos. If these companies haven't been targeted, they probably will be soon.
By accessing a Telegram channel used by attackers, researchers said they were able to find at least 9,931 compromised user credentials, of which 3,120 had associated email addresses, plus 5,441 compromised MFA codes. Because two-thirds of the data the researchers recovered didn't include email addresses, they couldn't identify those victims, beyond the region in which they reside.
High-Profile Targets, Victims
In addition to Twilio, another confirmed target of the campaign is Cloudflare, which said some users fell for the attack, but it was blocked thanks to the organization's use of security keys such as Yubikey to handle multi-factor authentication.
In multiple cases, attackers were able to effect a supply chain attack by pivoting from an initial employee target to the company's customers:
- Twilio: Attackers who hit the messaging platform were then able to target users of messaging platform Signal. Twilio says 1,900 users' phone numbers and SMS verification codes were compromised. As a result, attackers could have taken control of these accounts and impersonated the users.
- Klaviyo: The marketing firm earlier this month warned that hackers accessed its "internal customer support tools to search for primarily crypto-related accounts and viewed list and segment information for 44 Klaviyo accounts," downloading list or segment information for 38 of these accounts."
- Mailchimp:The email distribution platform is used by numerous firms, including cryptocurrency software and hardware providers to handle confirmation emails, password resets and alerts. One of its customers, cloud infrastructure provider DigitalOcean, has tied attempts to reset its customers' passwords to the Mailchimp breach.
Open Source Tooling
Group-IB says attackers used the open source JavaScript library Nuxt.js to build its phishing sites for the front end of the attack and the open source, Python-based web framework Django for the backend.
The attacks, it says, proceed accordingly:
- Users receive an SMS message with a link that leads to a phishing site designed to spoof their corporate login screen.
- Users are directed to enter their username and password.
- If they do, the next screen asks for their two-factor authentication code.
- The phishing site forces the browser to download a copy for the AnyDesk remote administration tool.
Phishing Kit: Signs of Inexperience
The attackers showed possible signs of inexperience by pushing users to download a Windows executable file to all devices including those with mobile operating systems. Group-IB concludes the attacker failed to properly configure the phishing kit to target mobile devices.
The phishing kit was set to send stolen data to a Telegram channel controlled by attackers, which is a commonly used approach, Group-IB says. Based on that Telegram channel, the firm says it was able to identify a specific Telegram user and correlate his activity with other Telegram channels, which led back to his Twitter account. It says the Twitter handle links to a GitHub account with the same username and profile picture of the unidentified North Carolina software developer.
Group-IB says "the findings about the alleged identity of the threat actor have been shared with international law enforcement agencies."
Correction: Aug. 26, 2022 07:30 UTC: An earlier version of this story stated incorrectly that Cisco was targeted as part of this attack campaign. While Cisco recently reported that it fell victim to an attack that bypassed its multifactor authentication, Group-IB has not tied the attack on Cisco to this campaign.