Business Continuity Management / Disaster Recovery , Critical Infrastructure Security , Cybercrime
Ransomware Trends: Volume of Known Victims Remains Steady
Despite More Efforts to Blunt Extortionists, Evidence Suggests Tide Has Yet to Turn
Despite an increased focus on tracking, targeting and disrupting ransomware by Western governments, the volume of new ransomware victims doesn't appear to have declined. Even so, multiple experts say that nation-state efforts to combat cybercrime syndicates are picking up speed and may well yet have an impact.
See Also: Modernizing Malware Security with Cloud Sandboxing in the Public Sector
For the public sector in the U.S., however, security firm Emsisoft notes that in 2021, at least 77 state and municipal governments and agencies, 1,043 schools and universities, and 1,203 healthcare providers are known to have fallen victim to ransomware.
It's notable that the annual count of such victims remains relatively unchanged from the prior two years, says Brett Callow, a threat analyst at Emsisoft.
"The number of ransomware incidents involving the public sector has held fairly steady for the last three years, and that's a concern," he says. "It means that, for whatever reason, the public sector has been unable to significantly improve its resilience and has remained as vulnerable as ever."
Then again, the same could be said of most sectors.
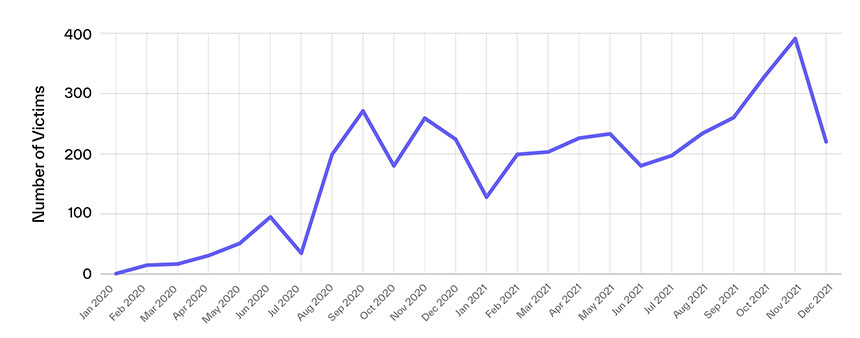
Cloud email security firm Abnormal Security, in a report reviewing the past two years of known ransomware attacks, says that the overall number of ransomware victims, at least in the United States, has continued to increase since the White House said it was devoting additional resources to combating cybercrime.
"The last quarter of 2021 saw the highest number of victims in the U.S. in the past two years," tweets Crane Hassold, the firm's director of threat intelligence.
The significant focus from US authorities on #ransomware in the first half of 2021 seems to have done little to deter actors from targeting US companies. The last quarter of 2021 saw the highest number of victims in the US in the past two years (+43% from the previous quarter). pic.twitter.com/sYKsqkBICH— Crane Hassold (@CraneHassold) January 25, 2022
All of the above numbers carry caveats. For starters, they're based on attacks that publicly come to light, typically either because a victim reveals them or because attackers post a victim's name onto a data leak site to pressure them into paying a ransom. But cybersecurity firm Group-IB estimates that only 13% of victims of a ransomware operation that runs a data leak site will end up being listed there.
Otherwise, many victims of a ransomware attack will never publicly acknowledge falling victim or may not specifically say they were hit by crypto-locking malware.
Seasonal Decline
Based on publicly known ransomware attacks, the volume of new victims did decline at the end of last year. Cybersecurity consultancy NCC Group reports that based on victims posted to publicly accessible data leak sites, it counted 318 victims in November 2021, compared to 200 in December 2021, meaning the total number had declined by about one-third.
While any reduction is welcome, unfortunately, NCC Group says such a drop is likely just a seasonal trend.
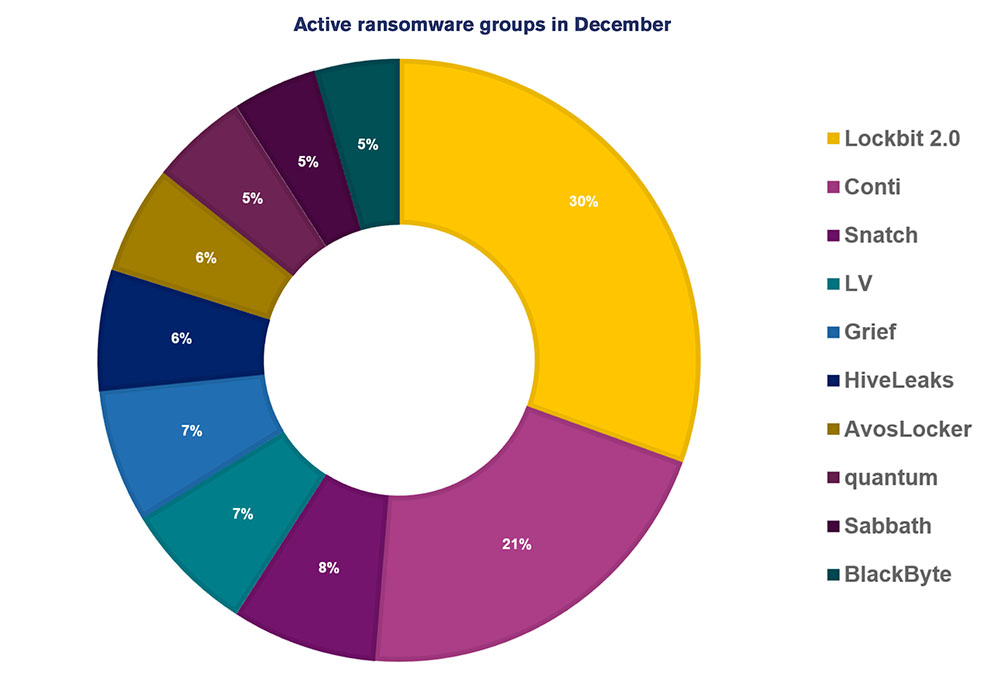
Meanwhile, two long-dominant operations continue to be at the top. "Of the decreased overall activity, LockBit and Conti continue to be the two most prevalent threat actors in the ransomware space, with 47 and 32 attacks respectively in December," NCC Group says.
Too Often Missing: Basic Defenses
If the known quantity of fresh ransomware victims isn't declining, one question is why organizations aren't successfully repelling more attacks.
One obvious culprit, Callow says, is a continuing, widespread failure to implement multifactor authentication wherever possible, despite cybersecurity experts - including Cybersecurity and Infrastructure Security Agency Director Jen Easterly - calling on all organizations to embrace it.
"I've said it before, and I'll say it again: Enabling multi-factor authentication makes you 99% less likely to get hacked," Easterly has tweeted.
Anecdotal examples of organizations that are failing to use MFA abound. Illinois NPR affiliate WGLT reported Wednesday that the state's District 87 school board had seen its cyber insurance premiums rise by 334% from a few years ago, from about $5,000 to $22,000 per year. But what the school district's insurance policy will pay out in the event of an incident remains reduced, until the school district implements MFA, which it plans to do by April, WGLT reports.
Incident response experts say too many organizations are failing in particular to use MFA to lock down remote desktop protocol (see: Why Are We So Stupid About RDP Passwords?).
"I still see RDP, or social engineering and phishing, being the pathway for the majority of ransomware gangs," says Joseph Carson, chief security scientist and advisory CISO at cloud identity security vendor ThycoticCentrify.
Fresh Moves to Combat Ransomware
Despite the volume of successful ransomware attacks appearing to remain relatively constant, multiple forces could - potentially - take a bite out of this type of cybercrime.
The Biden administration last spring launched a new task force to combat ransomware and has been working to bolster American businesses' cybersecurity resilience, as well as bringing pressure to bear on countries perceived to provide safe havens for cybercrime.
"Post-Colonial Pipeline, the U.S. government has ramped up its counter-ransomware efforts, including creating a $1 billion federal cybersecurity grant program as part of the Bipartisan Infrastructure Deal - and a lack of funding is something that local governments have long identified as a barrier to better cybersecurity," Emsisoft's Callow says. "While the battle is far from won, these and other measures will hopefully have a real impact and we'll see a reduction in the number of incidents in months and years ahead."
Earlier this month, Russia's Federal Security Agency, the FSB, said that it had acted on intelligence shard by the U.S. when it arrested 14 suspected members of the notorious REvil, aka Sodinokibi, operation. So far, eight have been charged with illicit money control or laundering.
The White House has welcomed the crackdown, saying it's been sharing intelligence with Moscow since last spring. Against the backdrop of Russia threatening to invade Ukraine, a senior White House official said the Biden administration is taking the arrests at face value.
"Our expectation is that Russia … would be pursuing legal action within its own system against these criminals for the crimes that they have … done," as well as "preventing future ones," the official said.
Criminal Attitude: Wait and See
Security watchers have said the suspects who have been arraigned appear to be lower-level players, or part of the teams of affiliates who serve as business partners for ransomware-as-a-service - aka RaaS - operations such as REvil. In other words, for whatever reason, REvil's main operators and administrators appear to remain at large.
Nevertheless, the arrests could at least drive some smaller players to close up shop and make others think twice about entering the market.
Already, the arrests appear to be causing at least some chaos and panic in the cybercrime underground, not least over uncertainties in how Russian law might be used to prosecute such crime, according to chatter being tracked by security firm Trustwave SpiderLabs.
In one recent forum discussion, Ziv Mador, vice president of security research at Trustwave SpiderLabs, says that "one person seemed to believe the charges would not be that serious: 'As I understand it, they are charged with Article 187 of the Criminal Code of the Russian Federation, and there is maximum of 7 years, i.e. it's not even a serious crime.'"
But Mador says another forum user disagreed. "Learn the Criminal Code. This is a serious crime. The creation of an organized crime group [can get you] from 12 to 20 years [in prison]," the forum user said.
Of course, the list of charges against the accused could also be expanded.
'Let's Not Celebrate Too Quickly'
What Russia does next will help determine if those arrests serve as any type of deterrent.
"There is a strong chance that the FSB's activity has a long-term impact on cybercrime, but only if the Russian government follows through and prosecutes those arrested to the full extent of their law," Mador says. "Russian prisons are no walk in the park, and cybercriminals know that."
Again, however, while security experts say these are obviously steps in the right direction and should be welcomed, it's not clear what if any effect this will ultimately have on the ransomware ecosystem.
"It's a win in regard to cooperation and seeing a ransomware gang being taken down," ThycoticCentrify's Carson says of the REvil arrests. "But the growth of ransomware groups is increasing; there's more to deal with. So to take one big group down is a good thing. But let's not celebrate too quickly."
Indeed, ransomware operators have a proven ability to innovate. But belatedly, Western governments are trying to do the same. And while the variety of new initiatives underway have yet to come to fruition, they will at least continue the press against ransomware activity, says Dave Liebenberg, head of strategic analysis at Cisco Talos.
"We are also monitoring the impact of U.S. President Joe Biden's whole-of-government approach to countering the ransomware threat, which so far has included initiatives enacted by the Treasury Department, Department of Justice, and other agencies to disrupt ransomware actor's ability to operate," Liebenberg writes in a blog post.
"Many of these initiatives will likely have ripple effects that have yet to be seen," he says. "We suspect that as U.S. officials prioritize countering the ransomware threat, we will see groups continue to shut down operations or rebrand under new monikers, become more restrictive about members joining their RaaS ranks, and attempt to improve their operational security."






















