Business Continuity Management / Disaster Recovery , Cybercrime , Cybercrime as-a-service
Ransomware Operations Double Down on Data Leak Sites
More Victims Getting Listed and Data Dumped on Leak Sites, Researchers Warn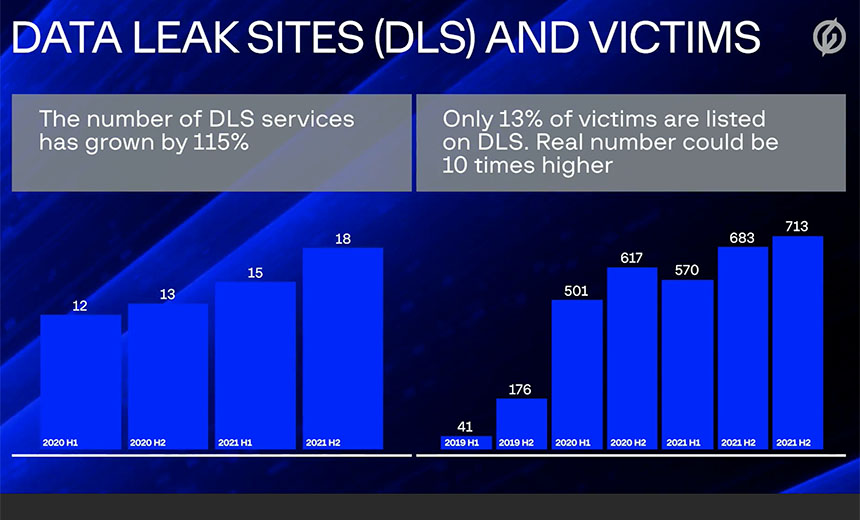
Many ransomware-wielding attackers continue to rely on a number of cybercrime-as-a-service providers to support their ability to easily gain access to targets and steal data. An increasing number of ransomware operations also run data leak sites to pressure nonpaying victims into meeting attackers' ransom demands, researchers say.
See Also: Ransomware Costing Organizations Billions as CIO's and CISO's Lose Their Jobs
One cornerstone of the ransomware ecosystem remains initial access brokers, who provide paying customers with remote access to a victim's network. While such access can come in many forms, security researchers say stolen remote desktop protocol credentials remain common, as do stolen virtual private networking connections.
Tracking just how much access gets sold remains difficult because many brokers do not publicly list victims or prices. Some brokers also have exclusive, private relationships with ransomware operations.
Based on what researchers can see, however, the market has been burgeoning. Comparing the 12 months ending on June 30 with the prior 12-month period, cybersecurity firm Group-IB says in a new report that it saw the number of publicly listed initial access offers nearly tripled, increasing from 362 to 1,099. The total value of those nearly 1,100 separate access offers was $7.2 million.
Greater Access Costs More
The greater the access, the more an access broker will charge for its initial access offering. For example, the most widely available credentials - RDP and VPN - offer low levels of access and regularly sell for as little as $5 or $10 per individual endpoint, according to a new report from security firm Trend Micro.
But offers for much more powerful types of access, such as administrator-level access to an organization's Active Directory identity and access management system, will cost much more, because very little additional effort would be required to steal data from the victim or push ransomware onto numerous endpoints.
"Simply put, the less work a buyer needs to do, the more expensive an offering is," Trend Micro says.
Again, many listings are private, and when advertisements are public, oftentimes sellers list no price. Even so, "for brokers that do list prices, we found that the average price for access to a business with admin credentials is at $8,500; however, prices can reach up to $100,000," Trend Micro says. Especially at the higher end, prices can also be highly negotiable, it adds.
The economics here are clear: If a ransomware-wielding attacker can use the access to force a ransom payment from a victim, the cost of the initial access will represent a very small investment on a much bigger return.
Continuing Extortion
When criminals gain illicit access to a network, of course they can do more than just unleash ransomware. While that attack strategy remains prevalent, so too do supporting tactics such as double extortion, in which attackers threaten to leak the data unless victims pay a ransom.
Not all ransomware operations maintain a data leak site. Even when they do, not all victims get listed. Some, for example, will have complied with attackers' demands to pay up quickly, to avoid the attempt to "name and shame" them.
But the volume of victims that do get posted to data leak sites has been growing. In September, for example, Allan Liska, an intelligence analyst at threat intelligence firm Recorded Future, reported that "the number of victims posted to ransomware extortion sites remained near an all-time high."
There's been a serious jump in the number of victims getting listed, however, since 2019. Notably, when comparing the 12 months ending on June 30, 2020, with the subsequent 12-month period ending on June 30, Group-IB found that the number of victims being publicly listed increased from 229 to 2,371.
During the same time period, the number of new ransomware-as-a-service operations - meaning they run affiliate programs - rose from four to 21, and the number of new data leak sites rose from 13 to 28, it says.
For the 12 months ending June 30, "the number of new, public ransomware affiliate programs grew, but the speed of growth decreased, but unfortunately didn't stop," Dmitry Volkov, CEO of Group-IB, said Thursday at the firm's annual CyberCrimeCon threat hunting and intelligence conference.
Data Leak Site Activity Grows
Of the ransomware operations that run data leak sites, from July 1, 2020, through June 30, Group-IB said the Conti group dumped data for the most victims, accounting for 17% of all victims globally who had data dumped online. "It is noteworthy that in the first three quarters of 2021, ransomware operators released 47% more data on attacked companies than in the whole of 2020," it says.
Here's how many victims had data dumped by the five most prevalent operations for the 12-month period ending on June 30:
- Conti: 361
- LockBit: 251
- Avaddon: 164
- REvil/Sodinokibi: 155
- Pysa: 118
For comparison, here's how many victims had data dumped by the five most active data-leaking ransomware operations from July 1, 2019, through June 30, 2020:
- Maze: 259
- Egregor: 204
- Conti: 173
- REvil/Sodinokibi: 141
- Pysa: 123
At a country level, the greatest number of victims that had data dumped for the 12-month period ending on June 30 hailed from the United States (968), followed by Canada (110) and France (103), Group-IB reports. The most-affected sectors were manufacturing (10%) and real estate (10%), followed by transportation (8%), it says.
What accounts for ransomware operations leaking more victims now than in the past? Volkov cited two factors. "The first one: Threat actors do more attacks with partners," meaning they have a greater number of affiliates who are each able to amass victims. "The second factor: Victims don't pay a ransom, more often, and that's why they've been listed on data leak sites," he said.

Group-IB estimates that only 13% of victims of a ransomware operation that runs a data leak site end up getting listed there. That suggests many of the other victims will have already paid a ransom in part to prevent their being publicly named. Overall, it estimates that about 30% of ransomware victims do end up paying a ransom.
Based on current trends, Group-IB's Volkov predicts that more ransomware operations will list more victims across a greater number of leak sites, with some operations running multiple leak sites at once "to dilute the attention of law enforcement and of course security researchers," since attackers "understand that the higher numbers and more companies released on data leak sites, the more attention they attract."
In addition, for any nonpaying victims, operators could well begin to offer any valuable, stolen data for sale, rather than leaking it outright. "Such activity was seen previously but has not yet become a trend," Volkov said.






















