Business Continuity Management / Disaster Recovery , Cybercrime , Fraud Management & Cybercrime
Ransomware: DarkSide Debuts; Script-Kiddies Tap Dharma
Crypto-Locking Malware Wielded by Even More Types of Extortionists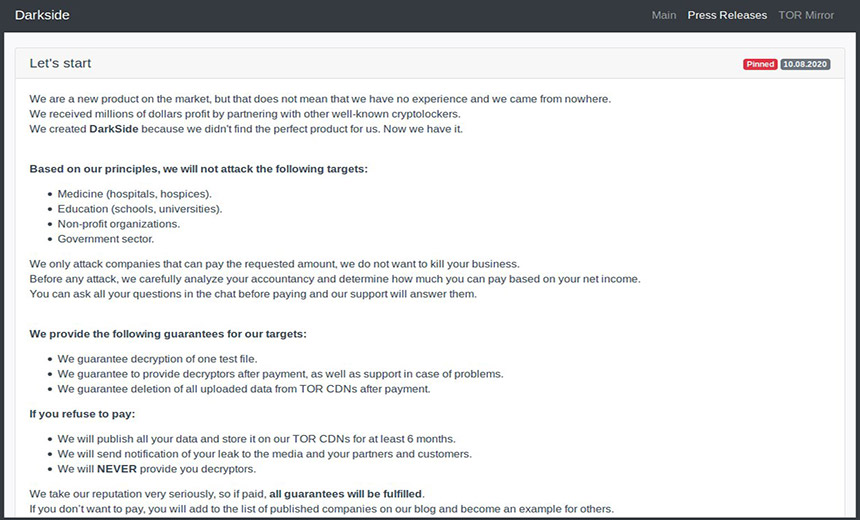
Ransomware-wielding gangs continue to rack up new victims and post record proceeds. That's driving new players of all sizes and experience - beginners, criminals already skilled in the ransomware ecosystem and more advanced attackers - to try their hand at the crypto-locking malware and data-exfiltration racket.
See Also: Cyber Risk Readiness
For criminals, the draw of ransomware is easy to see: Using crypto-locking malware to extort organizations continues to pay ever-greater dividends - on average, now nearly $180,000, according to ransomware incident response firm Coveware, based on cases it investigated from April through June. The average amount was a 60% increase from the first quarter of the year (see: Ransomware Payday: Average Payments Jump to $178,000).
Clearly, ransomware is surging, despite the ongoing economic chaos caused by the COVID-19 pandemic. In large part, of course, that's because some victims are paying their attackers for the promise of a decryption key, to remove their name - and potentially, exfiltrated data - from a "name and shame" site, for a promise from attackers to delete stolen data, or potentially all of the above.
On Thursday, the University of Utah disclosed that it was hit in July by an unspecified strain of ransomware that cryptolocked "employee and student information," after which it paid attackers a $457,000 ransom - partly covered by its cyber insurance policy - in return for not releasing data.
More examples: Blackbaud, which builds marketing, fundraising and customer relationship management software, last month claimed to have "recently stopped" a ransomware attack by paying off its attackers. Garmin, which builds fitness-tracker and navigation devices, also reportedly paid an undisclosed ransom amount to attackers who successfully encrypted its systems with WastedLocker.
Ever-Growing List of Victims
Not every ransomware attack, of course, results in victims paying. But many attackers appear to be playing the numbers. Via the attempt to name and shame victims who didn't pay, especially if they're well-known names, gangs also earn free marketing about their operations, potentially building buzz that might persuade future victims to pay them quickly to go away.
The list of ransomware victims is growing longer. Recent victims include Brown-Forman, a Louisville, Kentucky-based manufacturer of alcoholic beverages - including Jack Daniels - that was recently hit by Sodinokibi, aka REvil, which claimed to have stolen 1 TB of data, including sensitive employee records. Brown-Forman vowed to not pay a ransom.
The Sodinokibi ransomware-as-a-service operation has also listed on its dedicated data-leaking site "Happy Blog" the law firm GSMLaw as a victim, as well as fresh victims in the insurance, consulting, and oil and gas sectors. Sodinokibi is one of a number of operations that steals data before crypto-locking systems, then threatens to leak or auction stolen data unless victims pay (see: Avaddon Ransomware Joins Data-Leaking Club).
Meanwhile Carnival, the world's largest cruise ship company, on Aug. 15 suffered its second ransomware outbreak of the year and warned in a U.S. Securities and Exchange filing that both customer and employee data had likely been stolen.
Other recent ransomware victims include Boyce Technologies, which builds transit communication systems - and lately also ventilators - and got hit by the DoppelPaymer gang, and Canon USA, which got hit by the Maze gang.
DarkSide Makes Debut
Drawn by the potential profits, new players continue to arrive on the scene. Kaspersky last month warned that the North Korean hacking team Lazarus Group now appears to have expanded into ransomware, which it drops after using malware to gain a foothold in a network and steal Active Directory credentials.
Earlier this month, another new ransomware operation called DarkSide appeared, although it claimed that its members are not newcomers. "We are a new product on the market, but that does not mean that we have no experience and we came from nowhere," the group claimed in a post to a hacking forum that was posted by Malwrhunterteam security researchers. "We received millions of dollars in profit by partnering with other well-known cryptolockers."
In the "press release" announcing its arrival, the gang says that it only targets organizations "that can pay the requested amount." It adds: "We do not want to kill your business."
Bleeping Computer reports that the operation appears to have demanded ransoms ranging from $200,000 to $2 million.
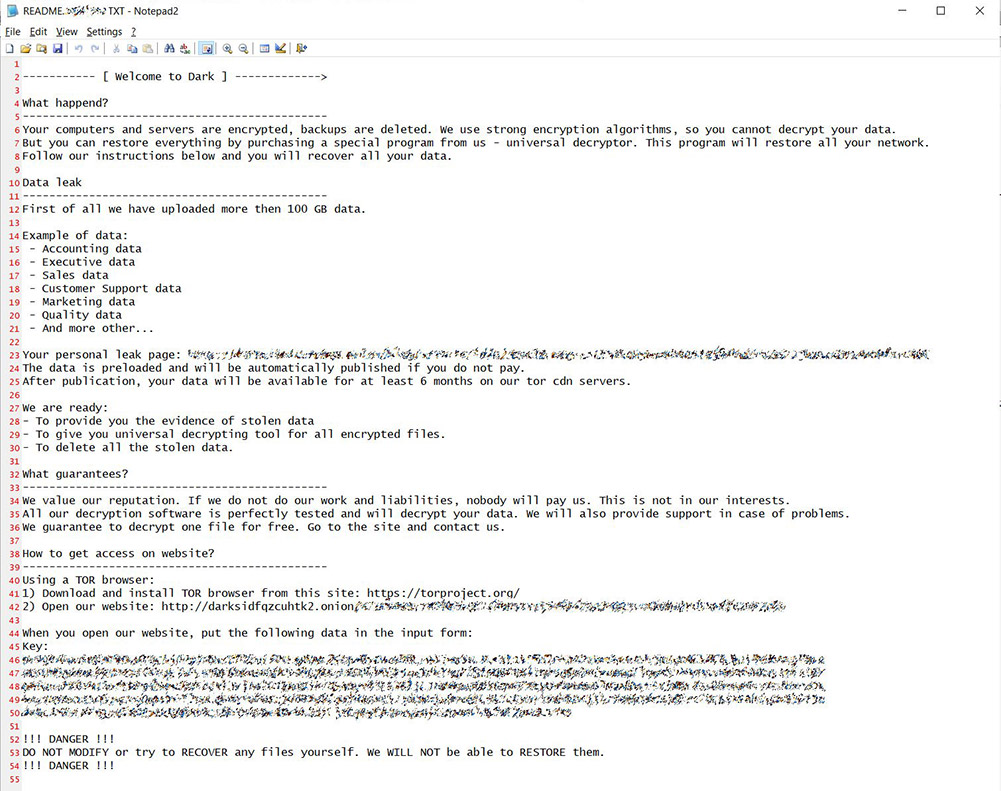
Security experts say there are some similarities between DarkSide and REvil, although no smoking gun that would prove that DarkSide is a breakaway operation. For example, DarkSide's ransom note is very similar to REvil's, but such text is easy to cut and paste. Bleeping Computer also reports that DarkSide uses an encoded PowerShell script that's identical to REvil, but again that could be copied.
DarkSide ransomware also has code to check for CIS countries...
— MalwareHunterTeam (@malwrhunterteam) August 11, 2020
What a surprise, right?
What is interesting is that it uses both GetSystemDefaultUILanguage & GetUserDefaultLangID, that is very rare in RWs. Only done by GandCrab and then REvil before I think...
@VK_Intel pic.twitter.com/p0Ut60vMHV
Also, both types of ransomware check infected PCs to ensure they're not in one of the member states of the post-Soviet Commonwealth of Independent States. The CIS includes Russia as well as Azerbaijan, Armenia, Belarus, Georgia, Kazakhstan, Kyrgyzstan, Moldova, Tajikistan, Turkmenistan, Uzbekistan and Ukraine (see: Russia's Cybercrime Rule Reminder: Never Hack Russians).
'Iranian Script Kiddies' Wield Dharma
Some ransomware-wielding attackers, however, appear to be newcomers to the hacking scene in every sense.
For example, in what appears to be a relatively new phenomenon, a group of Persian-speaking hackers operating from Iran appear to be wielding Dharma ransomware for financially motivated attacks against targets in China, India, Japan and Russia, says cybersecurity firm Group-IB.
Dharma, aka CrySis, first appeared as a ransomware-as-a-service operation in 2016, and continues to be "targeted at entry-level cybercriminals, and provides a paint-by-the-numbers approach to penetrating victims’ networks and launching ransomware attacks," Sean Gallagher, a senior threat researcher at Sophos, says in a recent research report (see: How Dharma Ransomware-as-a-Service Model Works).
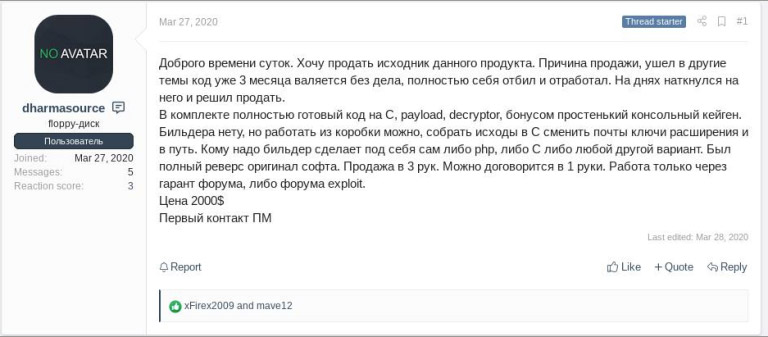
Since it debuted, multiple variants of Dharma have been in circulation. In March, the source code for one such variant appeared for sale online for $2,000 on a Russian cybercrime forum, Sophos says.
Whereas Dharma had previously been tied to relatively low ransom demands, in recent months, Coveware says it's started seeing some six-figure ransoms being demanded by Dharma-wielding attackers.
“The fact that Dharma source code has been made widely available led to the increase in the number of operators deploying it,” says Oleg Skulkin, a senior digital forensics and incident response analyst at Group-IB. “But it’s surprising that Dharma landed in the hands of Iranian script kiddies who used it for financial gain, as Iran has traditionally been a land of state-sponsored attackers engaged in espionage and sabotage."
No SamSam
Of course, this isn't the first time that Iranians have been tied to wielding ransomware. In 2018, the U.S. Justice Department charged two Iranians with using SamSam ransomware to attack more than 200 organizations and entities - including Atlanta and other municipalities - and collecting $6 million in ransoms and causing more than $30 million in losses to victims.
"The SamSam ransomware attacks were indeed a rare example of financially motivated offenses on the Iranian cybercriminal scene," Skulkin tells Information Security Media Group. "It cannot be ruled out, however, that their capabilities might have been used in pro-government espionage campaigns due to the vast reach of their attacks.
By contrast, he says, the Iranians wielding Dharma appear to be "newbie hackers" using relatively simple techniques, tactics and procedures, such as using the free Masscan internet port scanner to find potentially vulnerable hosts, then using software called NLBrute to try to brute-force guess valid access credentials for gaining a remote connection to the host (see: Ransomware Gangs' Not-So-Secret Attack Vector: RDP Exploits). In some cases, he says, attackers also attempted to use an exploit for CVE-2017-0213, a flaw in Windows COM Marshaler, which Microsoft announced and patched in 2017, to escalate privileges.
After gaining access, these attackers used various tools to move laterally before eventually dropping Dharma and a note demanding a ransom payment - typically from 1 to 5 bitcoins ($11,800 to $59,000) - in return for the promise of a decryption tool, Group-IB says.
Skulkin says this hacking group apparently has not exfiltrated data, which, together with "the use of short-sighted techniques, which do not go beyond getting money here and now," is evidence that "the threat actors seem to be very immature."
But as described above, the same can't be said for all of the new operators and services in the ransomware sphere.






















