Endpoint Security , Fraud Management & Cybercrime , Open XDR
Kaseya Was Working on Patches Before Ransomware Attack
REvil Ransomware Operation Beat Patching Effort in a 'Final Sprint,' Researcher Says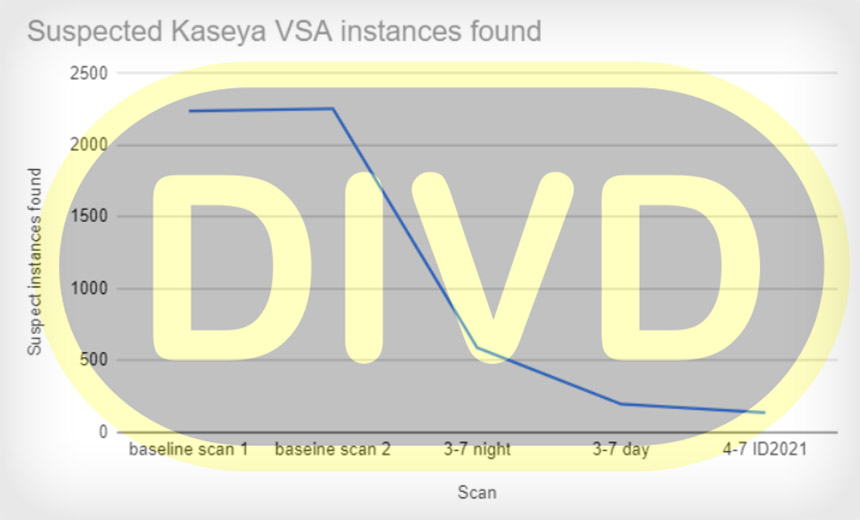
Kaseya, the remote IT management software vendor at the center of a devastating ransomware strike, was close to fixing the vulnerabilities in its software before attackers associated with the notorious REvil operation hit.
See Also: The Anatomy of the Solarwinds Attack
That means damage from the clever and devastating supply chain attack against Kaseya will likely grow in the coming days at an intense scale. The administrators for REvil, or one of its affiliates, exploited several vulnerabilities in Kaseya's VSA remote management software, which is used by managed service providers, to deploy ransomware on the systems of at least hundreds if not thousands of organizations.
Dutch researchers had recently notified Kaseya about several zero-day vulnerabilities in VSA, and the company was working on fixes. But REvil was faster. Some victims are now being asked for as much as $5 million in ransom, according to Bleeping Computer. It's unclear if REvil somehow knew in advance that the patches were coming.
"Unfortunately, we were beaten by REvil in the final sprint, as they could exploit the vulnerabilities before customers could even patch," writes Victor Gevers, chairman of the Dutch Institute for Vulnerability Disclosure, in a blog post on Sunday.
While its internal patching development effort was underway, Kaseya would have been holding its breath. Software companies typically don't make information about vulnerabilities available prior to patches because that means "it'll immediately leak to black hat evil hackers," says Rob Graham of Errata Security, a Georgia-based consultancy.
Hence Kaseya's customers would have unknowingly been left hanging in the wind in the in-between time, which is a not uncommon - but nonetheless risky - position to occupy.
"Patches are always a trade-off between the costs of downtime related to the patch and the risk of getting hacked," Graham says.
Ahead of Kaseya's Patches
Gevers notes that Wietse Boonstra, a researcher with the DIVD, had reported several vulnerabilities to Kaseya. The details of those flaws have not yet been publicly released, although they've been given a placeholder designation as CVE-2021-30116.
Technically it was a zero-day. We were in a coordinated vulnerability disclosure process with the vendor while this happened. The CVEs were ready to be published; the patches were made and prepared for distribution, and we mapped all online instances to help speed up the process.
— Victor Gevers (@0xDUDE) July 3, 2021
Contacted by Information Security Media Group on Sunday, Gevers says he can't reveal when DIVD notified Kaseya of the vulnerabilities. But he says it was within the standard coordinated vulnerability disclosure window, which is generally 90 days.
DIVD has been conducting research into vulnerabilities around the administration interfaces of products. The team has made notable findings, including a pre-authentication vulnerability in Pulse Secure's VPN and in Fortinet's VPN devices.
Gevers says there are often security problems around administration interfaces, which are especially problematic if those devices are reachable via the internet. If such software must be internet-facing, then he says organizations must ensure they adequately protect it.
"Don't put remote administration systems directly on the internet without some firewall ACL, network filtering or VPN unless you want to get hacked over and over," Gevers tells ISMG.
The Kaseya incident lacks some of customary activity that accompanies other ransomware attacks, which suggests the attackers may have moved with more haste to get ahead of Kaseya's patches.
For example, at least some victims saw no data get exfiltrated, security vendor Sophos says.
Ransomware groups often steal data before encrypting files in order to demand money for both decrypting files and stopping the public release of data. Sophos also notes that some victims did not see types of backup files known as volume shadow copies get deleted, which is another common tactic used by attackers to complicate victims' attempts to simply restore crypto-locked systems.
Vulnerability: Authentication Bypass Suspected
The REvil gang is a ransomware-as-a-service group, which means it supplies its crypto-locking malware as a service to affiliates, who use it to infect organizations. Every time a victim pays, the affiliate and the operation share the profits.
Many security experts have expressed worry that ransomware gangs, flush with cash, are fueling zero-day exploit development, and REvil has been one of the most successful and profitable groups in history (see: REvil's Ransomware Success Formula: Constant Innovation).
Security experts say REvil appears to have exploited a zero-day vulnerability present in on-premises versions of VSA that had internet-accessible administration panels.
The security consultancy Huntress Labs, in a write-up posted to Reddit, says it believes the initial vulnerability REvil targeted was an authentication bypass in the web interface of VSA, meaning that any MSP that had their VSA exposed to the internet would have been at risk.
Gevers notes that the number of vulnerable, web-facing instances of VSA dropped from 2,200 around Friday, when Kaseya detected the attack, to less than 140 by Sunday, which is a positive sign, suggesting fast moves by defenders to protect themselves.
Huntress Labs also says the authentication bypass would have allowed REvil to upload the original payload, although it then appeared to exploit other SQL injection flaws to begin executing the code.
The ransomware was disguised as "a fake management agent update," writes Kevin Beaumont, head of the security operations center at U.K. fashion retailer Arcadia, in a blog post.
"This fake update is then deployed across the estate - including on MSP client customers’ systems," Beaumont writes. But the supposed update "is actually REvil ransomware."
Huntress Labs says at least 30 MSPs in the U.S., Australia, the EU and Latin America fell victim to the attack. More than 1,000 customers of those MSPs are likely also affected, it says.
Mark Loman, director of engineering at Sophos, told ISMG that as of Sunday, it was tracking not 30 but rather more than 70 MSPs as having been hit, leading to disruptions for the hundreds of organizations that collectively relied on those MSPs (see: Kaseya Ransomware: 'Largest Attack I've Witnessed So Far').
In an update issued Sunday night, U.S. time, Kaseya said that the problems have been "localized to a very small number of on-premises customers only."
Kaseya says it is prepping a software update for the on-premises version of KSA. The company says its software-as-a-service data center will be brought back online on Monday, starting with the EU, U.K. and APAC center, followed by its data center in North America.





















