Cybercrime , Fraud Management & Cybercrime , Geo Focus: Asia
India-Based Grab Denies Cyberattack Claim by Malaysia's DragonForce
Firm Says 'Leaked Data' Gleaned From Third-Party Vendor, No Grab Systems Affected
Indian hyperlocal logistics provider Grab is denying claims spread by a Malaysian hacktivist group that it fell victim to a hacking attack.
See Also: Would You Rather be Cloud Smart or Cloud First in Government?
Hacktivist group DragonForce Malaysia says it stole details of Grab delivery personnel, posting last Saturday on social media platforms Twitter and Telegram a spreadsheet containing names and other data.
#OpsPatuk Pawned by DragonforceMalaysia
— DragonForceIO (@DragonForceIO) June 18, 2022
rider https://t.co/RqWDJwZTWW pic.twitter.com/nuazsTdX2Z
A Grab spokesperson tells Information Security Media Group the spreadsheet contains referrals for motorcycle delivery drivers originating from a third-party vendor. No Grab systems were directly targeted, the company says.
The data published by DragonForce shows details such as referral name, contact number and expected interview date and entry creation date.
Grab says its information security team is working to identify the details of the leak, including its source, and provide remediation. "We are further investigating this and will take appropriate action," the spokesperson tells ISMG.
OpsPatuk Campaign
DragonForce Malaysia is amid an active campaign dubbed OpsPatuk against Indian targets, launched as retribution for anti-Muslim remarks made by a now-suspended spokesperson of India's ruling Bharatiya Janata Party (see: Malaysian Hacktivists Target Indian Websites as Payback).
Earlier this month, the hacktivist group attacked and defaced at least 70 Indian public and private sector websites.
More recently, and around the same time as the alleged Grab data leak, the hacktivist group also claimed to have hacked and defaced the Delhi government railway police website.
#OpsPatuk India Police Gov Pwned / Leaked by DragonForce Malaysia.
— DragonForceIO (@DragonForceIO) June 18, 2022
Mangsa Pembunuhan Terlalu banyak disana.https://t.co/VCJJna3y2P#AnonGhost #DragonForceMalaysia #RileksCrew #T3DimensionMalaysia #CodeNewbie #PhantomCrews #MyGovTeam #LocalhostMalaysia #UnitedMuslimCyberArmy pic.twitter.com/ILIiOCfDIB
The Delhi government railway police did not respond to ISMG's request for information.
DragonForce Malaysia also claims to have hacked the Port of Chennai's online gate pass portal. The group says it has leaked nearly 67 megabytes of data from the port's database and posted on its Telegram channel screenshots of what it says are the port's internal database file directories.
Attack Vector
DragonForce Malaysia says it gains initial access by exploiting a recently discovered vulnerability affecting some Atlassian Confluence servers that is tracked as CVE-2022-26134.
The vulnerability is an Object-Graph Navigation Language injection bug affecting Atlassian Confluence versions 7.18 and older. It allows unauthenticated users to execute arbitrary code on a Confluence server or data center instance.
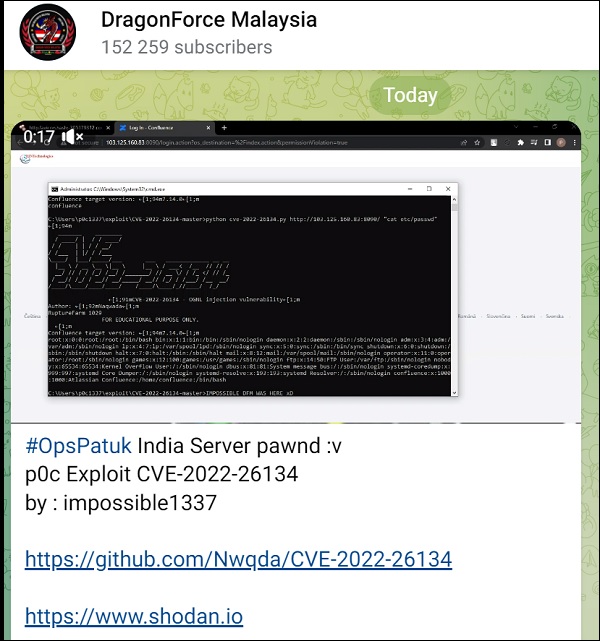
The hacktivist group says it leverages the Shodan online device search engine to find Indian organizations running on vulnerable versions of Atlassian software and then uses proof of concept exploit publicly available on GitHub to gain initial access into the victim systems.
Cybersecurity company Fortinet has also noted DragonForce's use of the Atlassian Confluence vulnerability.
The group primarily targets the government, technology, financial services, manufacturing and education sectors in India, Fortinet says.
The Malaysian group also deploys DDoS attacks, compromises VPN portals with stolen credentials, targets web application vulnerabilities, defaces websites and exploits Microsoft's Follina CVE-2022-30190 vulnerability to attack victims, it says.






















