Breach Notification , Cybercrime , Encryption & Key Management
Hacked Off: Lawsuit Alleges CafePress Used Poor Security
23 Million Victims Across US, UK, EU and Australia Receive Breach Notifications
CafePress has been hit with a lawsuit alleging that it failed to notify customers about a massive data breach in a timely manner. The Louisville, Kentucky-based personalized product retailer sells custom T-shirts and a variety of other printed materials.
See Also: After Wannacry: Getting Ahead of Ransomware
The company believes that about 23 million users' details got swiped. In addition, security experts have warned that instead of using a fit-for-purpose password-hashing algorithm, CafePress was continuing to use SHA-1, which is outdated and stores passwords in a manner that is relatively easy for hackers to crack (see: SHA-1 Has Fallen).
Customer Details Exposed
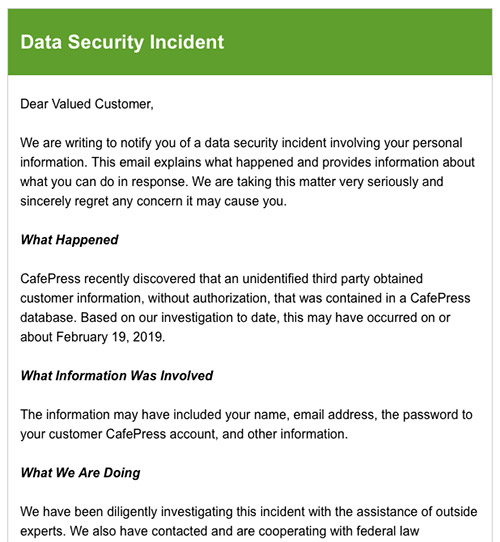
The company first notified customers about the breach last month. "CafePress recently discovered that an unidentified third party obtained customer information, without authorization, that was contained in a CafePress database," the company said in a Sept. 5 data breach notification on its websites. "Based on our investigation to date, this may have occurred on or about Feb. 19."
CafePress said that exposed information included names, email addresses, passwords for CafePress accounts as well as "other information," which it did not specify. But it said that for a small percentage of U.S. users, Social Security numbers or Tax Identification numbers were exposed.
The company added: "We are fully committed to protecting your information, and we deeply regret that this incident occurred."
Global Data Breach
CafePress primarily does business in the U.S., but also maintains branded websites for the EU, United Kingdom, Canada and Australia. In its breach notification, CafePress says the breach appears to have exposed information for users across all of those regions:
- United States: About 21 million accounts exposed.
- Europe: 1 million EU accounts, including 880,000 customers in the U.K. For some users, the last four digits of their credit or debit card was exposed.
- Canada: 495,000 customer accounts.
- Australia: 450,000 customer accounts.
CafePress says that across every region, exposed information "included names, email addresses, passwords to customer CafePress accounts, and other information," and that for less than 1 percent of affected individuals, a social insurance, social security or tax identification number was exposed.
Signs of Breach Spotted in July
The site "We Leak Info," which sells information about data breaches, on July 14 reported that 23 million CafePress users' first and last names, email addresses and password hashes had leaked.
New Data Breach Alert!
— We Leak Info (@weleakinfo) July 14, 2019
Site: Cafepress
Date: 02/2019
Records: 23,321,980
Status: Undisclosed
Info: Email, First Name, Last Name, Hash
See if your information was leaked for free at (link: https://t.co/Il5zj4Bl4h) https://t.co/3ev8DRCmZ6#weleakinfo #infosec #databreach #OSINT
Later, the breach was added to the free breach-notification site Have I Been Pwned. "The exposed data included 23 million unique email addresses with some records also containing names, physical addresses, phone numbers and passwords stored as SHA-1 hashes," the site reported on Aug. 5, noting that it received the data from "a source who requested it be attributed to 'JimScott.Sec@protonmail.com.'"
At the time, Scott, who's a security researcher, told Bleeping Computer that he'd found stolen CafePress data - involving about 493,000 accounts - for sale on cybercrime forums. But he said it wasn't clear if it had come from the same breach.
Scott told Bleeping Computer that he found a copy of the data on 23 million users online; half of the passwords had been hashed using SHA-1, and that the other half "contained third-party tokens for logins through Facebook and Amazon."
That's a concern because single-sign-on access tokens for Facebook Social Login and other services may persist for months or years and be difficult to reset, even following a breach (see: Experts' View: Avoid Social Networks' Single Sign-On).
As of Aug. 5, Bleeping Computer reported that CafePress was forcing users to reset their passwords, although it was making no mention of user passwords having apparently been compromised. In fact, that company wouldn't issue an official data breach notification until one month later.
Lawsuit Alleges Poor Security Practices
The nearly seven-month delay between the breach occurring and victims being notified, as well as a two-month delay between signs of the breach appearing in public and CafePress alerting customers, has been cited by law firm FeganScott, which on Oct. 4 filed a lawsuit seeking class-action status in U.S. District Court in Illinois. The suit alleges, in part, that "CafePress failed to update security software that is widely known as flawed, failed to employ best practices and failed to alert customers of the data breach."
“As galling as it is to know that a national retailer like CafePress failed in its duty to safeguard consumer information, it is reprehensible that they knew - or should have known - about the breach and failed to warn their customers that their credit card information and social security numbers could be for sale to the highest bidder on the dark web,” Beth Fegan, managing member of FeganScott, says in a statement.
Despite that assertion, CafePress has not said that any financial information was exposed in the breach. Fegan did not immediately respond to a request for comment.
U.S. security experts recommend that organizations notify victims as quickly as possible, with actionable information - ideally within 30 to 60 days of verifying a breach, unless specific state or federal laws require quicker notification (see: Data Breach Notifications: What's Optimal Timing?).
Outdated: SHA-1
Breached businesses inevitably say that the security of their customers' data is important to them. But actions too often speak louder than words, such as when organizations continue use SHA-1 to hash passwords.
"SHA-1 is the digital equivalent of a picket fence when it comes to keeping the wolves from the sheep.”
—Attorney Beth Fegan
For years, security experts have been warning that hashing passwords using SHA-1 or MD5 is inadequate because the hashed passwords can be relatively easily reversed by attackers to recover users' passwords. That's why experts urge organizations to instead use a dedicated hashing algorithm such as bcrypt (see: We're So Stupid About Passwords: Ashley Madison Edition ).
The alleged use of SHA-1 is also cited in the lawsuit filed by FeganScott. “CafePress allegedly relied on Secure Hash Algorithm 1 (SHA-1) as the lynchpin of its data security,” Fegan says. “Hackers and security experts know that SHA-1 has been useless in protecting data since about 2005. These days, SHA-1 is the digital equivalent of a picket fence when it comes to keeping the wolves from the sheep.”
Customers: Change Passwords
After data gets exposed, customers typically get left to do the heavy anti-fraud lifting (see: Zynga's Breach Notification: How Not to Inform Victims).
So too here: CafePress has issued the usual post-breach bromides about watching for fraud, in part by regularly obtaining free credit reports from Experian, TransUnion and Equifax. "We recommend you remain vigilant and take steps to protect against identity theft or fraud, including monitoring your accounts and free credit reports for signs of suspicious activity," it says in breach notifications that it appears to have begun sending directly to affected users beginning this month.
In addition, it recommends that users change their passwords if they have not done so recently, noting that individuals should be prompted to do so whenever they visit the CafePress website. "In general, you should always ensure that you are not using the same password across multiple accounts, and that you are using strong passwords that are not easy to guess," the notification points out.
Password reuse is a security killer, because it enables attackers to take credentials stolen in one breach - often a username, which is an email address, plus a reused password - and use it to log into any other service for which the user reused the credentials (see: Credential Stuffing Attacks: How to Combat Reused Passwords).