Cybercrime , Fraud Management & Cybercrime , Fraud Risk Management
Fxmsp Probe: Feds Say Group-IB Report Forced Its Hand
Hacking Suspect Named in Sealed Indictment Was Independently Outed by Researchers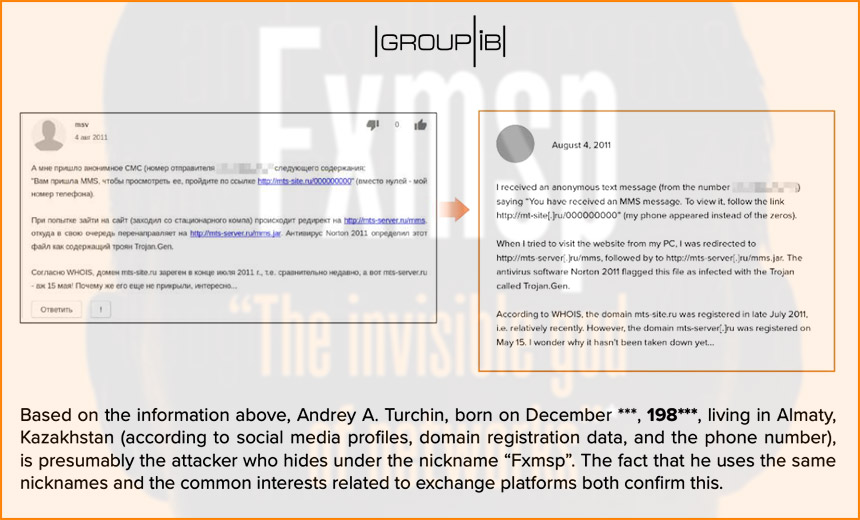
Did a private cybersecurity firm's report into the "Fxmsp" hacking operation that deduced the identity of the group's alleged leader disrupt a U.S. law enforcement investigation?
See Also: The State of Organizations' Security Posture as of Q1 2018
U.S. prosecutors on Tuesday revealed that a federal grand jury had charged Kazakhstan national Andrey Turchin, 37, with five felonies tied to computer fraud and abuse, wire fraud and access device fraud. Those revelations came after a Dec. 12, 2018, indictment against him was unsealed this week at prosecutors' request.
U.S. attorneys say the government's investigation is continuing, and that they expect to charge more individuals in connection with the probe of Fxmsp, which they describe as being "a prolific, financially motivated cybercriminal group composed of foreign actors that has hacked, and continues to hack, the computer networks of a broad array of corporate entities, educational institutions and governments in various countries, including the United States."
Prosecutors' move to unseal the indictment followed Singapore-based cybersecurity firm Group-IB on June 23 releasing a report, "Fxmsp: The Invisible God of Networks," describing the hacking group's operations. The title echoes a marketing tagline used by one of the group's affiliates to advertise via cybercrime forums Fxmsp's ability to give criminals quiet, remote access to hacked networks - for a fee, of course (see: Fxmsp Hackers Behind AV Source Code Heist: Still Operating?).
Group-IB's analysis found email addresses, domains and Jabber and social media accounts tied to Turchin that were also connected to Fxmsp. The firm concluded: "Andrey A. Turchin, born on December ***, 198***, living in Almaty, Kazakhstan (according to social media profiles, domain registration data, and the phone number), is presumably the attacker who hides under the nickname 'Fxmsp.' The fact that he uses the same nicknames and the common interests related to exchange platforms both confirm this."
Group-IB says its report was designed to help organizations better protect themselves against the types of attacks waged by Fxmsp (see: Studying an 'Invisible God' Hacker: Could You Stop 'Fxmsp'?).
"Our research was primarily focused on examining the threat actors' activities and TPPs [techniques, tactics and procedures] with the aim to provide businesses with comprehensive recommendations on how to avoid attacks similar to those conducted by Fxmsp," Group-IB CTO Dmitry Volkov told Information Security Media Group. "We do hope that our report will help prevent further victims and make its contribution to locating and arresting the threat actor hiding behind the nickname Fxmsp as well as his accomplices."

This isn't the first time that research published by a private firm has overlapped with an active law enforcement investigation. Even so, Alan Woodward, a professor of computer science at the University of Surrey, says that in general, the more research being published on "the bad guys," the better, especially if firms are also giving law enforcement a heads-up first, to help avoid disrupting active investigations.
"In some cases, the more eyes on the problem, the better," he tells ISMG, because that approach can help build a more complete picture of criminals' operations. He also notes, however, that such overlapping efforts increase the odds that "you're going to run across each other, now and again."
Prosecutors Have Indictment Unsealed
On Tuesday, federal prosecutors filed a motion to unseal the indictment against Turchin, aka "fxmsp."
"U.S. authorities have reason to believe that Turchin is aware of the existence of pending criminal charges in the United States," U.S. Attorney Brian T. Moran told Seattle federal court in a filing. "Given the group's prolific nature, sophistication and notable victims, 'fxmsp' and his accomplices, commonly referred to collectively as the 'fxmsp' group, have been a subject of interest of cybersecurity researchers," he added, and then referenced Group-IB's report.
"In addition to tracking 'fxmsp's' evolution and his group's exploits and list of victims, this report publicly identified 'fxmsp' as Andrey Turchin, of Kazakhstan, and provided a detailed explanation of the researchers' attribution determination," he said. "Since its publication, various news outlets in the United States and abroad, citing the report, have published articles about 'fxmsp' and his identification as Turchin." (Note: While ISMG has reported on Fxmsp, it declined to cite Group-IB's assessment of the hacker's alleged identity because it came from a single source.)
As of Tuesday, Turchin remained a fugitive, with Moran telling the court that it was working with "foreign authorities and to pursue his apprehension to face charges in the United States."
Moran told the court that the government had concluded that keeping the indictment under seal was no longer necessary, "given the unique circumstances of this matter, which include, among other things, Turchin's knowledge of the criminal charges in the United States and his public identification as the prolific hacker 'fxmsp.'"
On Wednesday, news site Bleeping Computer, which was cited - together with Forbes - by prosecutors as being one of the sites that named Turchin based on Group-IB's report, reported that Turchin may now have been detained by local authorities in Kazakhstan.
In 2015, the U.S. signed a "mutual legal assistance in criminal matters" treaty with Kazakhstan, but currently there is no extradition treaty between the countries.
How did Turchin have knowledge of the sealed indictment returned against him 18 months ago? The Justice Department could not be immediately reached for comment.
But on Feb. 19, 2019, Moran submitted a motion to the court to unseal the indictment and arrest warrant issued for Turchin - aka Fxmsp, "Andej Turchin," "Adik Dalv," and "Vadim bld" - "for the limited purpose of facilitating arrests, extraditions, searches and interviews of existing and future defendants."
At the time, Moran wrote that the limited nature of the unsealing was important. "Premature unsealing would create a substantial risk that the defendant and/or his co-conspirators will learn of the criminal investigation and charges and will take steps to thwart the efforts of law enforcement, alter criminal activity, evade arrest and destroy or tamper with evidence," he told the court. "Notably, it is significant that, given the nature of the criminal conduct, the threat actors, including the defendant, are in possession of confidential victim information and are believed to have ongoing unauthorized access to numerous victim computer networks."
Probe Led by FBI's Seattle Field Office
Following the unsealing of the indictment against Turchin on Tuesday, the FBI's Seattle office, which is leading the Fxmsp investigation, thanked the bureau's British counterpart, the National Crime Agency, as well as the National Security Committee of the Republic of Kazakhstan, and two private-sector firms: Intel471 and FireEye's Mandiant.
credits our partners with this investigation to include UK's National Crime Agency, the National Security Committee of the Republic of Kazakhstan (KNB), and support from private sector intelligence partners Intel471 and FireEye/Mandiant @NCA_UK @Intel471Inc @FireEye— FBI Seattle (@FBISeattle) July 8, 2020
Other firms that contributed intelligence to the FBI included Advanced Intelligence, aka AdvIntel, which is a fraud-prevention and risk-management firm based in New York. In May 2019, the firm issued a report detailing an attempt by Fxmsp to sell alleged remote access to three anti-virus vendors' networks - McAfee, Trend Micro and Symantec/Norton - as well as to their stolen source code (see: Crime Gang Advertises Stolen 'Anti-Virus Source Code').
Yelisey Boguslavskiy, AdvIntel's CEO, has told ISMG that the impetus for his company's report was to shine a light on Fxmsp's operations, and drive them off of the cybercrime forums they relied on for advertising stolen access credentials for hacked networks. He says his company provided a private report with many more details to law enforcement.
"Advanced Intelligence was honored to support our nation's law enforcement and the FBI Cyber Crime Task Force specifically with all advanced HUMINT" - referring to human intelligence, meaning insights gleaned potentially from person-to-person interactions on the cybercrime underground - "that we received in our investigation of the 'Fxmsp' group," AdvIntel said on Wednesday.
While the company's public 2019 report detailed Fxmsp's history and operations, it did not suggest what the real-world identify of any of the group's members might be. Yelisey Boguslavskiy, AdvIntel's CEO, said that members of the group had been acting in publicly trackable ways as well as privately for clients.
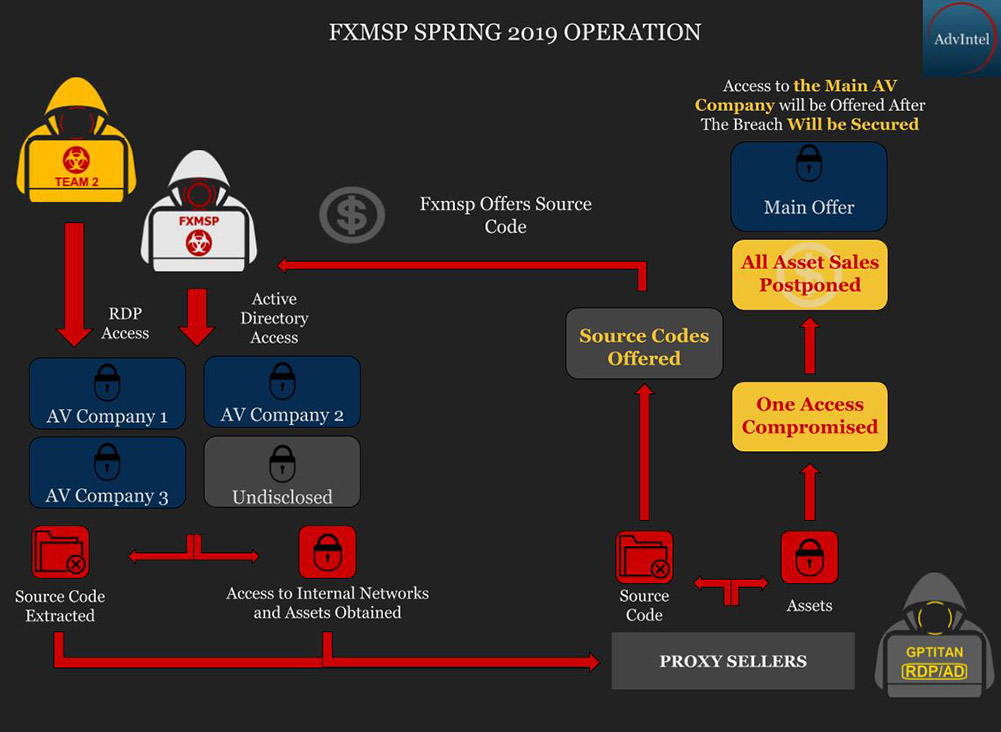
"Fxmsp was acting privately - beyond forums - until May 9, 2019, when we terminated their operations," Boguslavskiy has told ISMG (see: Hacking Timeline: Fxmsp's Rise and Apparent Fall).
Did Report Complicate Investigation?
Eighteen months after Turchin was charged via a sealed indictment - which was not public knowledge - and 16 months after prosecutors obtained court approval to selectively unseal the indictment and arrest warrant to facilitate international arrests and extraditions, again not for public distribution, Group-IB released its report into Fxmsp.
Intel 471, the cyber intelligence firm that contributed Fxmsp intelligence to the FBI and which was publicly thanked by the bureau for such efforts, suggests that by revealing the identity of Fxmsp, Group-IB's report disrupted the active law enforcement - aka LE - investigation.
"Commercial companies outing cybercriminals for publicity and marketing under the guise of supporting the greater good and without proper coordination and deconfliction with LE is rarely constructive and often harms law enforcement efforts," Intel 471 says. "The FXMSP case serves as a lesson learned for vendors. A detailed report published by a security vendor has seemingly forced LE to unseal a criminal indictment, publicize a case and likely introduced new challenges for their investigation. We hope that in the future more companies will operate more responsibly and that buyers of security products and services factor this in when choosing who to partner with."
Group-IB Shared Information With Authorities
But Group-IB says it fully informed law enforcement organizations prior to publishing anything, querying whether taking that step might disrupt any of their efforts.
"Ahead of making public any threat reports on cybercriminals, Group-IB contacts law enforcement agencies to make sure that such releases will not hamper any ongoing investigations, and the case with Fxmsp was clearly no exception," a company spokeswoman tells ISMG.
"In May, the expanded version of the report about the threat actor was handed over to two international law enforcement agencies, with which the United States has ties," the spokeswoman says. "Group-IB, in particular, provided the two organizations with the list of victims that the company was able to identify and the information which ultimately was the basis for establishing Fxmsp's presumed identity, including his Jabber, and accounts on various underground forums. In keeping with ethical principles, neither victims nor personal information of the threat actor were included in the report's public version."
Group-IB says it informed the law enforcement agencies of its plan to make parts of the report public "and inquired if there were any ongoing investigations with respect to the threat actor to ascertain that the report's publication wouldn't do any harm to the legal proceedings." Group-IB says the message that it received was that those law enforcement organizations "had no issues with Group-IB making the report public," leading it to "release the report with the aim to provide businesses with comprehensive recommendations on how to avoid attacks similar to those conducted by Fxmsp."
The Importance of Passive Tracking
Although the University of Surrey's Woodward advocates that cybersecurity firms and researchers maintain ties with law enforcement, as Group-IB and others do, he says that law enforcement doesn't always share information about operations they might have in progress, for fear that the information could get out. In addition, he says research published by private cybersecurity firms may later prove crucial for helping to build a case - as well as support it in court.
In this case, he doesn't think Group-IB's report harmed the investigation. "I've seen cases in the past, where various undercover operations thought they were tracking criminals, but what they were really doing is tracking other undercover operations," says Woodward, who's previously worked with the U.K. government and the EU's law enforcement intelligence agency, Europol.
"But this sort of thing, it's not active tracking; it's passive. You're sort of looking at their footprints in the snow and seeing where they've gone and if you can put a case together," Woodward adds. "That's when I think it makes sense to name them, and especially in this case, they did ask - not that they need permission, but they just wanted to make sure they weren't going to tread on any toes and that there wasn't someone about to swoop on the guy. But as it turns out, the guy was already aware, he wasn't going to go anywhere, so I don't think it did any real harm."





















