Cryptocurrency Fraud , Fraud Management & Cybercrime
DeFi Platform Deus Suffers Second Exploit in 2 Months
More Complex Than Flash Loan, Zero-Day Exploit Caused Loss of About $10 Million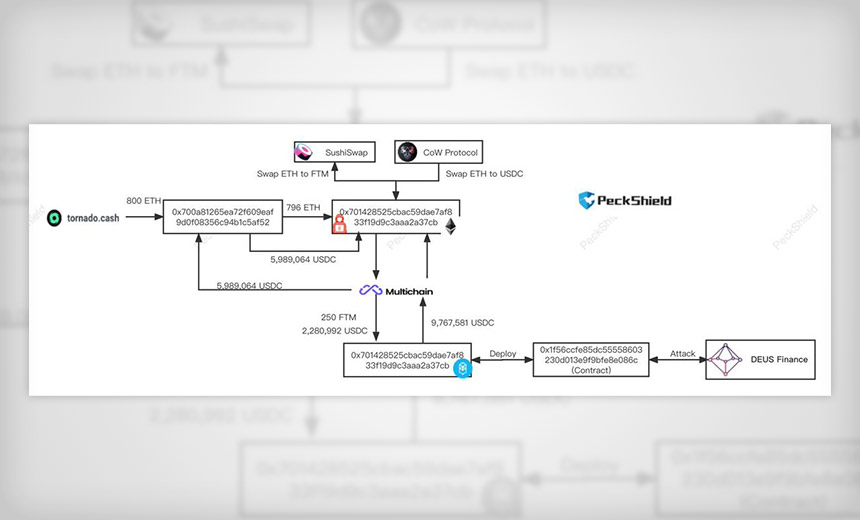
Decentralized financial services marketplace Deus Finance has been hit by hackers for the second time in two months, likely raking up losses of about $10 million in the latest incident.
See Also: Delving Deeper: 2023 Fraud Insights Second Edition
As a result of the attack, Deus has temporarily halted its DEI lending services.
Deus Finance offers infrastructure for others to build financial instruments, such as synthetic stock trading platforms, options and futures trading. Its ecosystem consists of two tokens: Deus, which is a protocol token governed by its underlying blockchain technology, and DEI, which is a cross-chain stablecoin whose value is pegged to the U.S. dollar.
Attack Details
The latest security incident was the result of a zero-day exploit, Deus Finance co-founder Lafayette Tabor tells Information Security Media Group.
"It was a zero-day exploit, meaning the attacker used a [vulnerability that was] not publicly known until now to fake the swap output price on Solidly," he tells ISMG. Solidly is a decentralized cryptocurrency exchange.
It appears that an unidentified attacker exploited a zero-day in a way that is currently undetermined, used a flash loan feature to borrow millions of dollars and manipulate the price of some crypto assets, and made about a 10% profit on the borrowed amount after selling the accumulated tokens at an inflated price.
Flash loans are essentially collateral-free cryptocurrency asset loans. The only caveat is that the borrower must repay the borrowed amount before the end of that transaction. Bad actors can manipulate the markets as the loan transaction is taking place - driving down the value of the borrowed asset and buying it back at a deflated price - or artificially inflate the value of the token to sell it at a higher price.
Tabor tells ISMG that although the attack included flash loans, it was "not a flash loan attack. It was more complex. The attacker manipulated the Muon VWAP oracle and the on-chain oracle price of DEI, then used their collateral to take a loan and sold it all," he says.
VWAP, or volume-weighted average price, refers to the average price a security is being traded at on any given day. Blockchain oracles are tools or layers that help access, verify and authenticate external data sources to make smart contracts operations broader and more accurate.
Ronghui Gu, co-founder of crypto security company CertiK, summarizes how the attack happened: "The hacker used a flash loan to conduct the attack. In this kind of attack, the hacker takes out a loan from a lending protocol, and then uses the funds to manipulate the value of an asset on a decentralized exchange. This manipulation was possible in this case due to the way the platform's 'oracle' was set up to determine the price of the token. An oracle is a third-party device that enables blockchains to access real world data. The problem here was that the oracle used was determining the price of the token based on a source that was able to be manipulated. By using the funds provided by the flash loan, the hacker was then able to make the token appear much more valuable than it actually was, and then use the artificially inflated value and trade it for a reliable asset."

In a tweet thread, Tabor explains some of the other technical details of the attack.
It is not yet known what the zero-day vulnerability was and whether it has been fixed.
Impact of the Attack
No user funds were affected and no users were liquidated, Deus tells ISMG. "These are strictly protocol funds in question," it adds.
While Deus pegs its losses to be around $10 million, blockchain security company PeckShield says that the exploit allowed the hacker to gain about $13.4 million, with likely higher protocol losses.
The @DeusDao was exploited today in https://t.co/USKNHhXeid with ~$13.4M gain for the hacker (The protocol loss may be larger).
— PeckShield Inc. (@peckshield) April 28, 2022
In the minutes-long attack, "the initial funds (~800 ETH) to launch the hack are withdrawn from @TornadoCash and tunneled to Fantom via @MultichainOrg. The stolen funds are tunneled back to @ethereum and stay in the hacker’s account," it says. The activity on the hacker's account can be seen here.
PeckShield did not respond to ISMG's request for clarification about how it arrived at the loss number and why the protocol loss may be higher.
The dev team is working on the DEI situation.
— DEUS Finance DAO (@DeusDao) April 28, 2022
1. User funds are safe. No users were liquidated.
2. DEI lending has been temporarily halted.
3. $DEI peg has been restored.
More details to follow.
A subscriber on its Telegram page, however, says that one of the points Deus mentioned in its tweet was "inaccurate"… "because point 3 says $DEI peg has been restored, which is not true." A stablecoin, DEI's value is pegged to the U.S. dollar.
The Deus team says in response: "Give the team some time to fix all of this. The dev team is working hard on DEI situation. And please stay tuned for upcoming announcements."
In an update, Tabor tells ISMG that the peg has now been fixed.
Next Steps
Deus tells ISMG that it is currently "working with multiple protocols, teams, CEXs, and the like, in an attempt to recover any of the lost funds."
It also intends to implement some upgrades to Muon's VWAP oracle, as well as sources for the on-chain oracle price, it says.
"We're looking to work with some protocols, deploying them into our processes as an extra layer of security and alert/prevention against these types of attacks in the future," the company adds.
More details on recovery efforts and the full scope of the exploit will follow soon, the company says.
Gu, however, says that Deus will "not be able to recover the stolen funds."
"The hacker has transferred the stolen funds to Tornado Cash, a privacy solution used to conceal where funds are sent on the blockchain,” he says.
Lossless, a company that offers crypto hack mitigation tools, says that "… we believe we can catch the culprit with you." On its Telegram page, it says that the company is investigating the incident with Deus. It tells ISMG: "If the need arises, a statement would be issued on the investigation." It did not respond to additional queries.
Gu of CertiK says that to date, there have been "more than $200 million losses on attacks by hackers making use of flash loans."
"The fact that the Deus attack does not neatly fit into a conventional definition of a flash loan attack is a testament to the speed at which hackers are finding ways to use flash loans to conduct exploits and the need for developers to constantly adapt to the changing front line of blockchain security," he tells ISMG.
The "most effective" measure against such attacks is to have projects audited by third parties, Gu says, especially when any alterations are made to the code or if the scope of the project changes.





















