Anti-Phishing, DMARC , Email Threat Protection , Multi-factor & Risk-based Authentication
Nation-State Spear Phishing Attacks Remain Alive and Well
Russians Tied to Hack Attacks, But 'Two-Factor' No Silver Bullet, Google Warns
Spear phishing attacks are in the news again following the Justice Department's indictment of 12 Russian military intelligence officers for allegedly using spear phishing as part of a wide-ranging kompromat campaign designed to interfere in the U.S. political process.
See Also: When Every Identity is at Risk, Where Do You Begin?
U.S. intelligence chiefs are warning that nation-states' malicious phishing campaigns continue unabated (see 10 Takeaways: Russian Election Interference Indictment).
But what can potential victims do about it?
For starters, anyone who's at risk should be using two-factor authentication to safeguard their email and cloud accounts. Using two-factor authentication typically requires users to enter not just a password when they try to log in, but also a one-time code from a software or hardware token.
Caveat: Two-Factor Has Limits
While that's an important step, there's no magic bullet for protecting against spear phishing.
"2FA is super important, but please, please stop telling people that by itself it will protect people from being phished by the Russians or governments," says Shane Huntley, who's part of Google's threat analysis group, via Twitter. "If an attacker can trick users for a password, they can trick them for a 6-digit code. 2FA will protect you against other important attacks, such as password being stolen from one site and used on another, or passwords databases being compromised. But any 2FA system that involves the user entering a code is phishable."
Activate Two-Factor Authentication Now
Many - but not all - sites and services, including Google, Microsoft's Office 365 and Salesforce, among many others - allow administrators to require users to use two-factor authentication to log in.
But security experts say high-risk users need more than a system that sends them a one-time code via an app or their phone. That's because attackers can trick users into entering the one-time code, too.
Attack Steps:
— Shane Huntley (@ShaneHuntley) July 22, 2018
1. User enters password into attackers site
2. Attacker attempts to log in immediately and SMS code sent to user
3. Attacker sees code is required then returns page asking for code to user
4. User enters code
5. Attacker wins
Huntley, for example, recommends that at-risk Google users safeguard their accounts using a physical security key that's compatible with the Fido Alliance standard U2F - for universal second factor (see Google Reportedly Plans Stronger Authentication Options).
No coincidence: That's the focus of Google's Advanced Protection program, which the company says it offers to help protect "anyone at risk of targeted attacks, like journalists, activists, business leaders and political campaign teams."
Using the program requires that a user obtain two security dongles - one is the primary, the other a backup - and carry one, at least whenever they might want to log on to Google.
Google recommends that the primary key be a wireless U2F security key. Unfortunately, there appears to be a dearth of wireless options that rate well, at least by Amazon users. But there are a number of "top rated" keys that plug into a USB port.
"Yes, security keys can be inconvenient, but this is what will save you," Huntley says - at least, potentially, on Google or anywhere else you're able to use such technology.
Phishing Epidemic Continues
The trouble with phishing is that it relies on social engineering - meaning it's designed to trick users - and it can potentially be used to compromise any online account.
Unfortunately, we humans are both easy to trick - at least some of the time - as well as fallible. And attackers can pummel would-be victims with phishing attacks until one succeeds.
The scale of the phishing challenge is reflected by the number of video interviews touching on phishing that I recently conducted at the London Infosecurity Europe conference. Experts described everything from the increasingly targeted nature of phishing attacks and the importance of never forgetting the human factor as well as training users, using technology to extract data from emails and attachments and implementing the practice of tracking malicious domains to better block phishing campaigns.
But as this patchwork of practices, procedures and technology demonstrates, there's no single fix for the phishing problem.
Poster Child: John Podesta
Furthermore, with more of our business and personal lives now living in the cloud, the impact of falling victim to a phishing attack continues to increase.
One of the most high-profile phishing victims in recent years was John Podesta, Hillary Clinton's 2016 presidential campaign chairman. Federal prosecutors say the same group of GRU officers that targeted the Democratic Congressional Campaign Committee and the Democratic National Committee also targeted Podesta's personal email account.
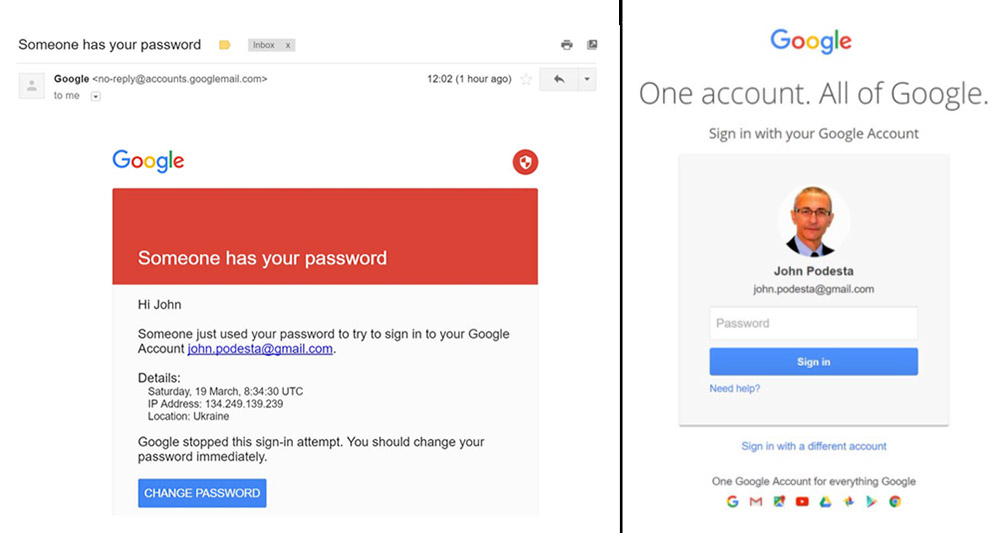
In late 2016, The New York Times reported that aides to Podesta, who had access to his private Gmail account, received a fishy-looking email disguised as a security notification from Google and and sent it to Clinton campaign IT aide Charles Delavan asking if it was legitimate legitimate. He reportedly meant to reply that it was "illegitimate," but instead made a typo.
"This is a legitimate email," his reply reportedly read. "John needs to change his password immediately."
The campaign team said it was seeing numerous apparent phishing attacks on a weekly basis. So it's unclear if that particular error was what led to attackers gaining access to 60,000 emails stored by Podesta - a decade's worth of correspondence. But attackers did obtain the information, which WikiLeaks later dumped online.
Podesta's personal email account, however, was far from the alleged Russian attackers' only victim. According to the University of Toronto's Citizen Lab, the attack campaign tied by others to Russia targeted victims in 39 countries (see Tainted Leaks: Researchers Unravel Cyber-Espionage Attacks).
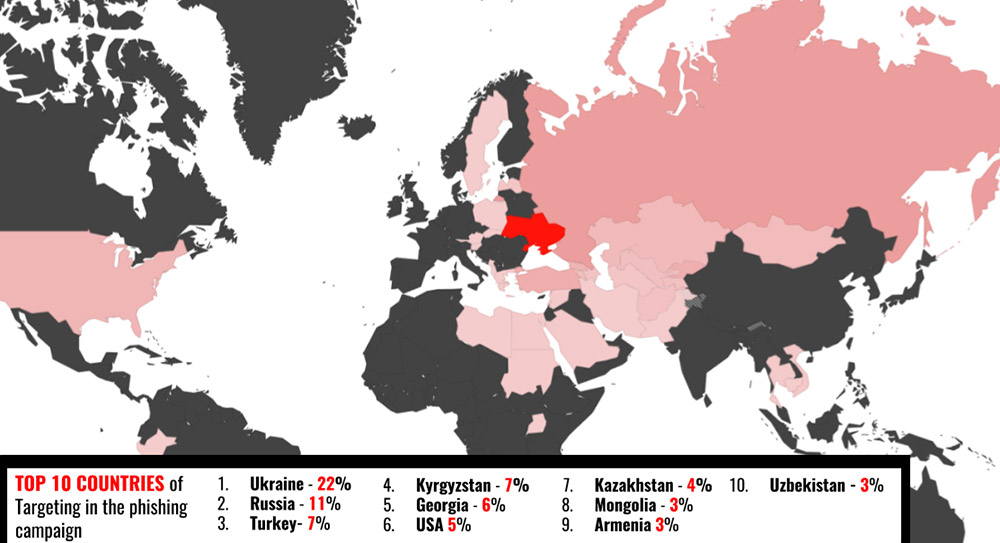
Based on data gathered by Dell's SecureWorks, Thomas Rid, a professor of security studies at Johns Hopkins University, has reported that as part of the campaign, attackers targeted at least 4,000 different email accounts "and were wildly successful, with one in seven victims ultimately revealing their passwords."
Targets in US, Germany, Italy and Beyond
More context: The words "spear phishing" occur 22 times in the Justice Department's July 13 indictment, which says the tactic was used to penetrate not only the DNC, DCCC and Hillary Clinton's presidential campaign, but also "state and county offices responsible for administering the 2016 U.S. elections."
Add to that list U.S. county and state electoral boards as well as voting machine and election software vendors.

Beyond the DNC, DCCC and Podesta, the group's other breach targets included accounts used by "the German parliament, the Italian military, the Saudi foreign ministry," as well as Philip Breedlove, NATO's former Supreme Allied Commander Europe, and Colin Powell, former U.S. Secretary of State and chairman of the Joint Chiefs of Staff.
Anyone can fall victim to a phishing attack. That's why we all need to get smarter about defending against them.











