Card Not Present Fraud , Cybercrime , Endpoint Security
The Art of the Steal: FIN7's Highly Effective Phishing
Cybercrime Gang Phoned Victims to Increase Phishing Attack Success Rates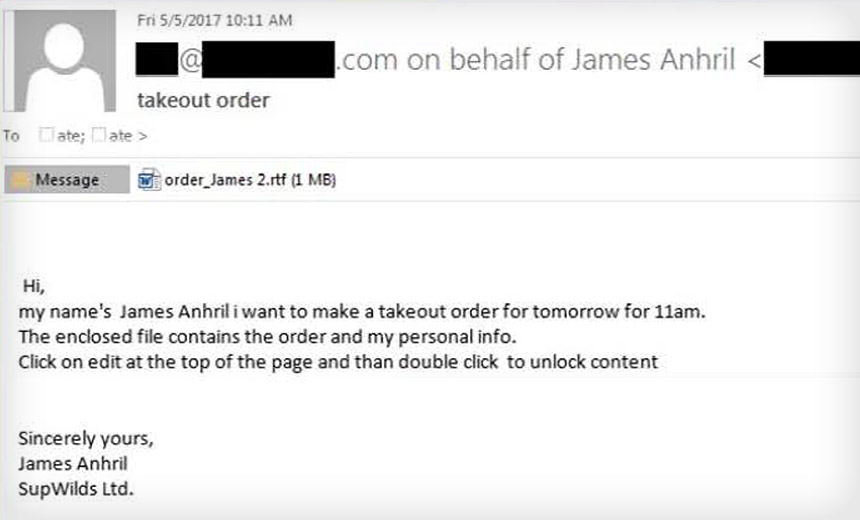
Criminal indictments against three alleged high-level members of a prolific cybercrime gang called FIN7, unsealed last week, reveal the low-tech attack tactics that had high levels of success.
See Also: Quantifying The Total Cost of E-Commerce Fraud
At an Aug. 1 press conference, prosecutors alleged FIN7 stole 15 million payment cards from more than 150 companies in the U.S. and abroad. Security experts, meanwhile, as of 2015 had already tied the gang's activities to more than $1 billion in fraud.
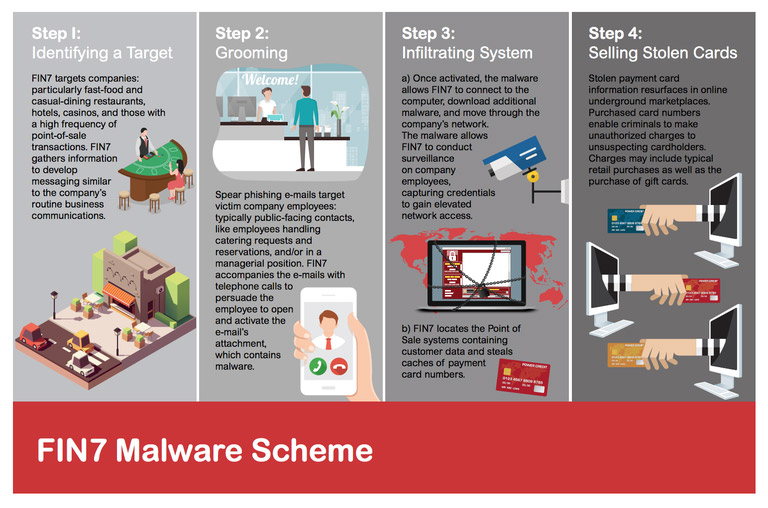
One of FIN7's primary targets has been businesses that gather payment card data. "FIN7 most commonly focused on fast-food and casual dining restaurants, hotels, casinos and businesses with a high frequency of point-of-sale transactions," the U.S. Department of Justice says.
That's no surprise, because stolen payment card data can be sold on underground marketplaces, giving attackers a quick way to monetize their hack attacks.
Popular Target: Catering and Group Bookings
Law enforcement officials alllege that the FIN7 gang would make telephone calls to individuals handling catering or group bookings inside businesses in an attempt to trick them into opening malicious emails that would unleash malware in the employee's network and potentially give attackers remote access. Sometimes, the emails carried a version of Carbanak malware, which is designed to steal access credentials as well as take screenshots of a victim's PC screen, prosecutors say.
"If you look at the detail in these emails, they [FIN7] did a lot of work to decide who to target, how to target, and they sent the email, they followed with a phone call, they knew quite a bit about the company, because most companies have public-facing websites, where you can figure out who the head of catering is," as well as find their email address, FBI Special Agent in Charge Jay S. Tabb Jr. of the FBI's Seattle field office, said at the press conference.
"Because legitimate businesses need to get business" - and for businesses that offer catering, some of those communications are sure to be handled by emailing the catering department - "it's probably not uncommon to have a Word document attached that says 'catering request,'" Tabb said.
The Justice Department says FIN7's victims included Arby's, Chili's, Chipotle Mexican Grill, Jason's Deli and Sonic Drive-In, among many others.
Security firm Trend Micro has also tied the group to payment card thefts from Lord & Taylor and Saks Fifth Avenue, noting that the stolen payment card data ended up for sale on March 28 on the carder forum Joker's Stash. Previous victims of FIN7, it said, had included Trump Hotels and Whole Foods, among others.
Education Has Limits
Because phishing emails rely on trickery, security experts say that user education remains essential (see Hello! Can You Please Enable Macros?).
"It's hard to defend against this; it's part of why we want to talk about how it happens so that folks really understand what they're looking for," said Annette L. Hayes, U.S. attorney for the Western District of Washington.
But no one is immune to being tricked. Numerous studies have found that even highly technical users occasionally fall for phishing attacks. False positives can also be a problem. In those cases, users discard legitimate emails because they suspect that they're fake.
Reality: Salespeople Need to Sell

Whatever rules a business sets for handling an attachment, it's unlikely that someone whose job is in sales, for example, is going to refrain from opening an email about a potential sales opportunity, provided the email it looks good enough to be real.
"Imagine that your job is booking hotel rooms for group travel, or handling large catering deliveries for business meetings from your restaurant," says Gary Warner, director of research in computer science at the University of Alabama at Birmingham, in a blog post. "A new potential customer calls and says: 'I'd like to book 40 hotel rooms for our sports team that is coming to play in a tournament in your town next month. What email should I send the details to?'"
Or someone says they want to place a big lunch order and would prefer to email the details through. "What sales person is not going to open that attachment?" Warner asks. "Right: Every single one will do so." And that's exactly how FIN7 allegedly operated.
Two-Factor Authentication
As a result, telling employees to beware of fake emails is an incomplete strategy.
Many security experts recommend organizations take another step, requiring employees to use some type of two-factor authentication to access their email and other business-critical systems. That way, attackers may have a tougher time stealing and reusing authentication credentials (see Reddit Says Attackers Bypassed SMS-Based Authentication).
Anyone at greater risk of being targeted online should already be using two-factor authentication to secure their accounts, security specialists advise (see Nation-State Spear Phishing Attacks Remain Alive and Well).
Stranger Danger
Another good piece of advice for fighting phising: Never open attachments from strangers. But like "learn to spot dangerous-looking attachments," that's not a foolproof strategy.
"Every organization has a least a few persons [who are] required to 'open attachments from strangers.' HR open CVs from strangers, sales open RFIs from strangers, etc.," says Tal Be'ery, security research manager at Israel-based blockchain cryptography firm KZen networks, via Twitter.
Plenty of scammers have also infiltrated legitimate email accounts and used their contact lists to distribute social engineering attacks to the victim's friends. One example: the "stranded traveler" scam, in which a friend apparently needs money immediately to pay a hotel bill after being robbed of their smartphone and passport while vacationing abroad. These phishing emails get sent from what appears to be a trusted account.
Quarantine Attachments in the Cloud
Maciej Cegłowski, who administers social bookmarking site Pinboard, says a good phishing defense for many organizations might be to always open attachments in the cloud from a device that doesn't run a desktop operating system.
"Talking about attachments is like abstinence education. 'Never open attachments' is correct but untenable advice. ... The safest way to view email is likely on an iPhone, iPad or Chromebook with attachments opening in GDrive," Cegłowski says via Twitter. "If you save [an] attachment to your laptop and upload it to GDrive, take care to delete the local file, or two weeks later you'll wonder 'what was this?' and double-click it."
Don't consider an attachment safe because it came from a trusted party. When they come for your account, it will be in the guise of an attachment or phishing link from someone you know well, and that you've opened dozens of times in the past.
— Pinboard (@Pinboard) August 3, 2018
But Warner says that while such a strategy might be viable for smaller organizations - especially newer ones without "a legacy of complex Word and Excel docs" - it likely wouldn't fly for larger businesses, or be foolproof.
"While Google does an excellent job, every company I've worked with has had some emails 'get through,'" he says. "Would moving to Google Docs help stop some of those malicious docs from triggering? Definitely. But are most corporate environments be ready to abandon Microsoft Office? I really don't think so."
Phishing Defense: Do Something
More sophisticated strategies are available, such as blocking known phishing domains. Organizations can also use technology to scan attachments or ensure that all inbound content gets intercepted and defused (see Safer Content Handling: Extract Information, Leave the Rest).
Regardless of technology, Warner says that rather than just educating users, "activating" employees to serve as part of an organization's phishing defense is key. "Making sure employees know how and have the tools to handle those suspicious emails is a key to success," he says. So too is ensuring that the security team follows them up.
Whatever the defensive strategy, as the FIN7 case makes clear, phishing attacks succeed by targeting people.
So don't leave users to fend for themselves.






















